Top 10 Remote Work Security Best Practices in 2023

What If You Were Hacked?
Are you working from home right now? If so, you’re not alone. The pandemic has changed the way we work, and for many of us, that means working remotely. And while remote work has its benefits, like flexibility and no commuting, it also comes with its own set of challenges. One of the biggest challenges is ensuring the security of your work data.
With so many of us now working from home, cybercriminals are taking advantage of this shift by targeting remote workers with phishing emails, malware, and other attacks. That’s why it’s more important than ever to prioritize remote work security.
In this article, we’ll share the top 10 remote work security best practices that you need to know. By following these best practices, you can protect your sensitive data and have peace of mind while working from home. So, grab a cup of coffee, and let’s get started!
Secure your Wi-Fi network

One of the key areas that require attention is your Wi-Fi network.
Your Wi-Fi network is a gateway to your work devices and data. Therefore, it’s essential to secure it from potential threats. Here are three best practices to secure your Wi-Fi network:
Password-protect your Wi-Fi
Setting up a strong password is the first step towards securing your Wi-Fi network. Avoid using default passwords or common phrases that are easy to guess. Instead, use a unique combination of uppercase and lowercase letters, numbers, and special characters. Don’t share your password with anyone unless it’s necessary. Check out this article on how to change your wifi password.
Update your router firmware
Router manufacturers release firmware updates regularly to address security vulnerabilities and improve performance. It’s essential to update your router firmware to the latest version to ensure optimal security.
Use a VPN
A virtual private network (VPN) provides an added layer of security by encrypting your internet connection. It masks your IP address and makes it difficult for hackers to track your online activities. Use a reliable VPN service when working remotely to ensure your data is safe.
Here are some popular VPN services:
Use strong passwords and a password manager

It’s more important than ever to have strong passwords and a reliable password manager to keep your online presence secure. We’ve all been there - using the same password for multiple accounts, or even worse, using a password that’s easy to guess. But by using strong, unique passwords and a password manager, you can ensure that your online accounts are safe from prying eyes. Did you know? A recent study found that 73% of users duplicate their passwords in both their personal and work accounts.
First and foremost, it’s important to understand the importance of using unique passwords for each of your online accounts. If you use the same password for multiple accounts and that password is compromised, then all of your accounts are at risk. That’s why using a password manager is a great solution. A password manager allows you to create complex, unique passwords for each of your accounts and stores them in a secure vault.
Now, you might be thinking, “But I heard that password managers aren’t safe either!” While there have been instances of password managers being compromised, the risk is still much lower than using the same weak password for multiple accounts. Sometimes there has to be a trade-off for the average guy. If you are a security freak who has a notebook of unique password that you type by hand every time, fine…but that’s just not an option for 99% of people. Plus, most password managers use advanced encryption to keep your passwords safe.
But not all password managers are created equal. It’s important to choose a reputable password manager with a track record of security, and to keep it updated with the latest security patches. Digital Trend’s article Using LastPass? You need to switch urgently, says security firm highlights the importance of choosing a reliable password manager, and switching if necessary.
By using strong passwords and a password manager, you can take a significant step towards securing your remote work environment. However, it’s just one piece of the puzzle. In the next section, we’ll cover the importance of antivirus software and how it can further protect your online presence.
Here are some popular password managers:
Install and update antivirus software
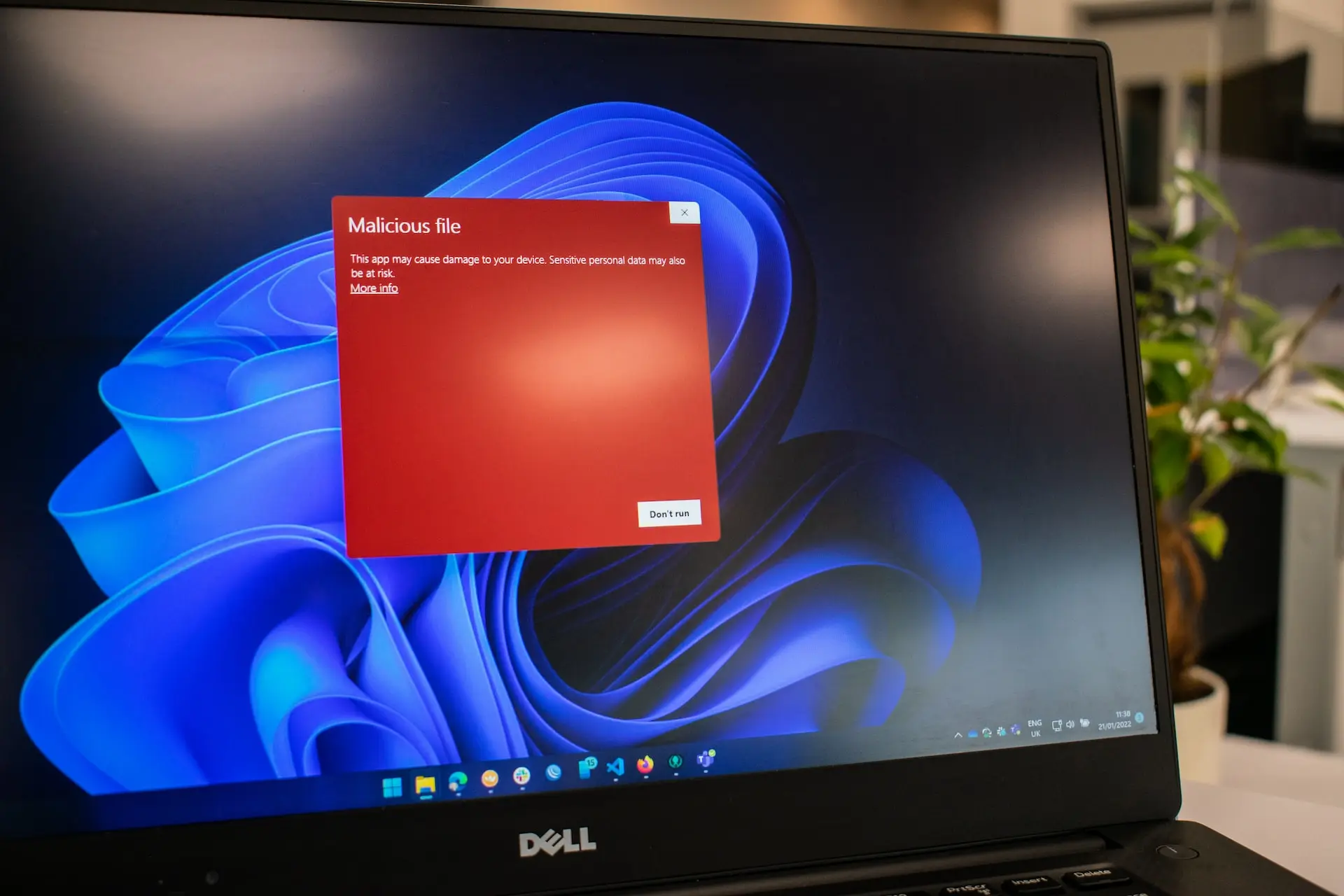
When it comes to remote work security, installing and updating antivirus software is a critical component to protect your computer and personal data from harmful cyber threats. Here are some best practices to follow:
Choosing the Right Antivirus Software
With so many antivirus software options on the market, it can be difficult to choose the right one for your needs. Look for reputable antivirus programs with features such as real-time scanning, automatic updates, and protection against various types of malware.
Some popular antivirus software products include:
Regularly Updating Virus Definitions
Once you’ve installed your antivirus software, make sure to regularly update its virus definitions to ensure that it’s equipped to detect and defend against the latest threats. Most antivirus software has automatic update features, but it’s a good idea to check that they’re enabled.
Antivirus software is just one piece of the puzzle when it comes to remote work security. Another important component is keeping your software and operating systems up to date.
The Role of Software Updates in Security
Software updates are released regularly to address security vulnerabilities and fix bugs in programs. Ignoring these updates can leave your computer and data vulnerable to cyber threats. To avoid this, make sure to download and install software updates as soon as they become available.
Automating Updates for Convenience
It can be time-consuming to manually check for updates for each program on your computer. However, most operating systems and software programs allow you to automate updates, so you don’t have to worry about missing any important security patches.
Remember, cybercriminals are always looking for new ways to exploit vulnerabilities, so it’s important to stay vigilant and proactive in your approach to remote work security. In the next section, we’ll take a look at another important best practice: keeping your software and operating system updated.
Keep software and operating systems updated
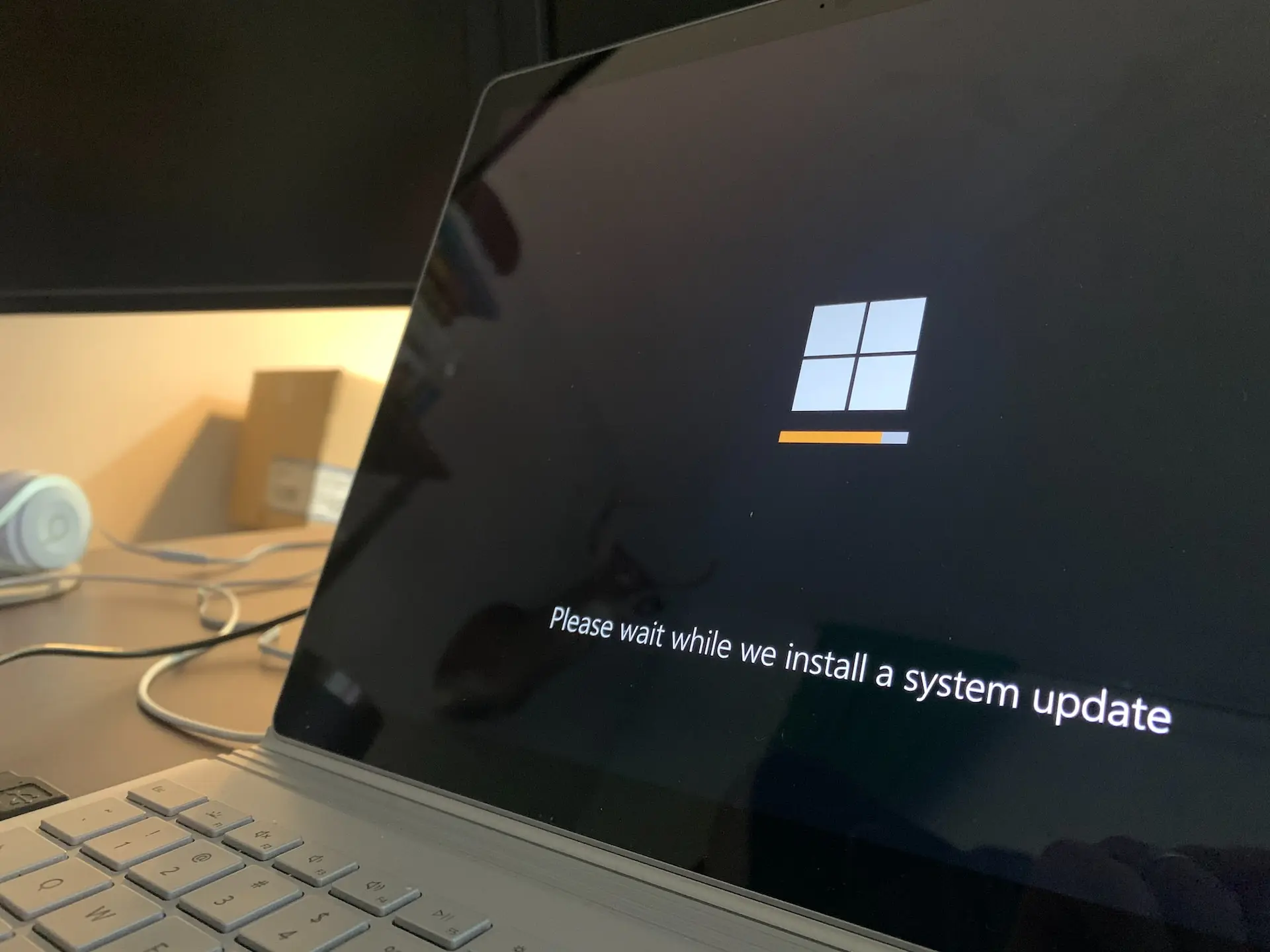
Keeping your software and operating systems updated is one of the most critical remote work security best practices you can implement. It may not be the most exciting task, but it’s one that can protect you from serious cyber threats.
Updating your software and operating systems ensures that security vulnerabilities are patched and fixed. Hackers are always on the lookout for weaknesses they can exploit, and outdated software and operating systems are a prime target. By keeping your systems up to date, you can prevent these vulnerabilities from being exploited and minimize your risk of a cyberattack.
Fortunately, updating your software and operating systems is relatively easy. Most software programs and operating systems have an automatic update feature, allowing you to set it and forget it. It’s also a good idea to enable automatic updates on your antivirus software, ensuring you always have the latest virus definitions.
By implementing this essential remote work security best practice, you’re taking a proactive step towards safeguarding your data and devices. But, this is only one step in a comprehensive remote work security plan.
Implement two-factor authentication (2FA)
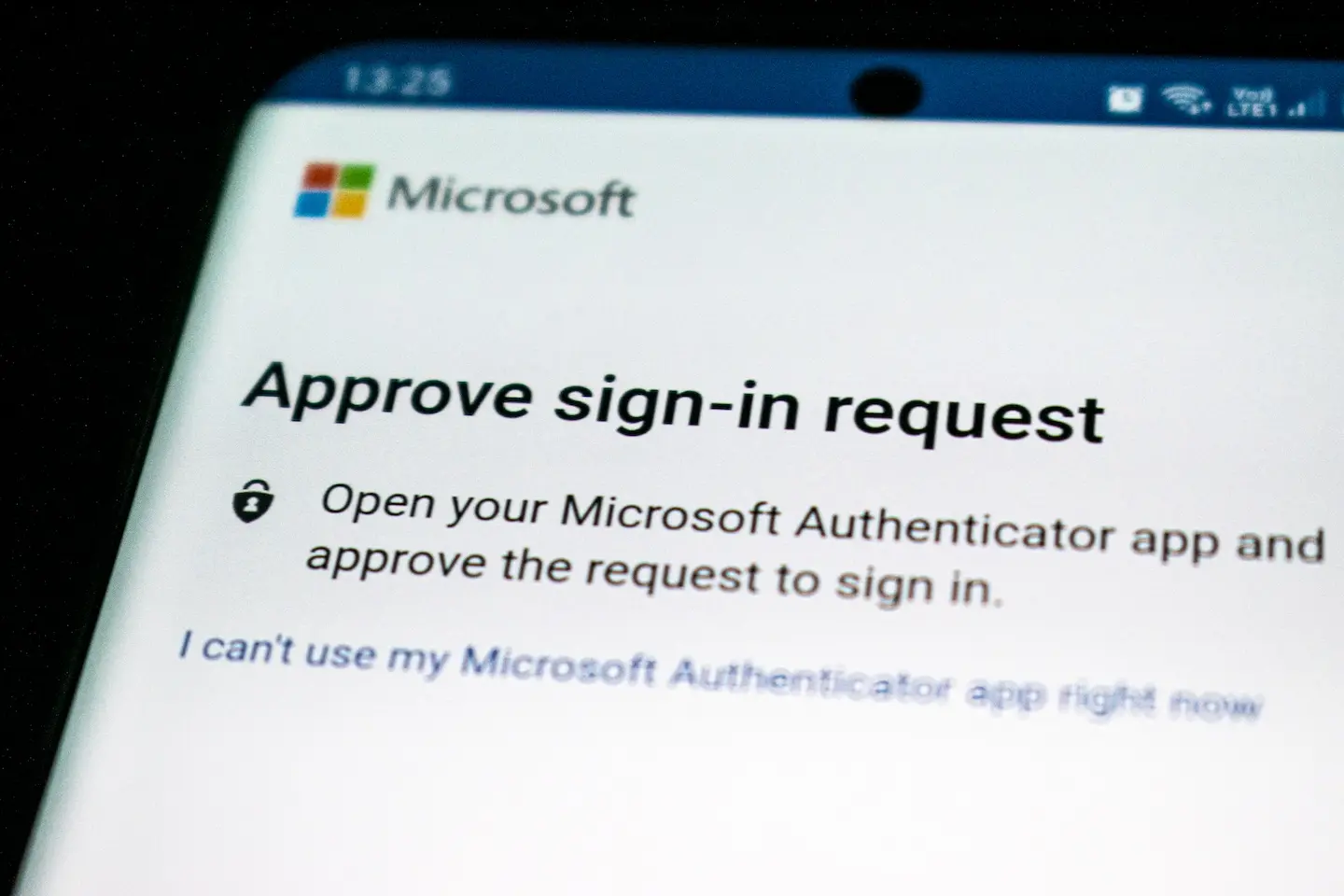
Protect your accounts with an extra layer of security
Implementing two-factor authentication (2FA) can greatly increase the security of your online accounts. This extra layer of security ensures that even if a hacker gets a hold of your password, they won’t be able to gain access to your account without the second factor, such as a text message code or a biometric scan.
Popular 2FA methods
There are many different 2FA methods available, including text message codes, app-based authentication, and biometric authentication. Each method has its own advantages and disadvantages, and it’s important to choose the method that works best for you and your team. Here are some of the most popular 2FA methods:
- Authy
- Google Authenticator
- 1Password <- We use this one since it’s integrated with the password manager we use.
How to enable 2FA on commonly used platforms
Enabling 2FA on your accounts is a straightforward process. Most online platforms and services have an option to enable 2FA in their security settings. It usually involves setting up a second factor and verifying it, such as linking your phone number or installing an authentication app.
While 2FA provides an extra layer of security, it’s still important to be vigilant against phishing attempts. In the next section, we’ll discuss how to identify and avoid phishing attempts to further protect your online security.
Be cautious of phishing attempts

In the virtual world of remote work, we are more vulnerable to the risks of phishing attacks than ever before. Cybercriminals are getting more sophisticated in their approach, using social engineering techniques to trick even the savviest of professionals.
Identifying Phishing Emails and Messages
Phishing emails often look like they come from legitimate sources such as banks, social media platforms, or even from within your own company. They may include links to websites that look like the real deal, but are actually malicious sites that can install malware on your device or steal sensitive data.
Verifying the Source Before Clicking Links or Downloading Attachments
It’s essential to take a moment to verify the source before clicking on links or downloading attachments. Hover over the link to see if the URL matches the sender’s email address or the context of the message. If it doesn’t, don’t click. Check with the supposed sender through a different channel, such as a phone call or instant message, to verify the authenticity of the email.
Don’t Share Personal Information
Be wary of requests for personal or sensitive information, especially in the form of an email or message. No legitimate company or individual would ask for your social security number or bank account details via email.
It’s crucial to be cautious of phishing attempts to protect sensitive data while working remotely. However, in the event of a successful attack, it’s essential to ensure that the data stored and shared is secure.
Securely store and share sensitive data

Keeping sensitive data secure is of the utmost importance. From confidential client information to proprietary company data, the risk of data breaches is real. That’s why it’s critical to have a plan in place for securely storing and sharing sensitive data.
Using encrypted cloud storage services
One of the easiest ways to store sensitive data is by using encrypted cloud storage services. These services, like Google Drive, Dropbox, or Box, allow you to upload files and access them from anywhere, while also encrypting your data to keep it secure.
When choosing a cloud storage provider, make sure to read up on their security protocols to ensure that your data is being protected. For example, some providers use zero-knowledge encryption, which means that even the provider themselves cannot access your files.
Safely sharing files with coworkers
When sharing files with coworkers, it’s important to ensure that they are also being stored securely. Instead of sending files as email attachments, which can be easily intercepted or forwarded to unauthorized recipients, use a cloud storage service to share the files directly.
To further increase security, use password-protected links or set expiration dates for the links so that the files are only accessible for a limited time.
By taking these precautions, you can ensure that sensitive data is only accessible to authorized parties.
Limit access to your work devices

Limiting access to your work devices is an essential best practice. Creating separate user profiles for work and personal use can help prevent unauthorized access to your work-related files and data.
One important aspect of limiting access to your work devices is the use of strong passwords. Creating unique passwords for each account can be a daunting task, but it is crucial to ensure the security of your data. A password manager can help keep track of your passwords and generate strong passwords that are difficult to guess.
In addition to using strong passwords, locking your device when not in use is also important. This simple action can prevent unauthorized access to your work device, even if someone gains physical access to it.
Another way to limit access to your work devices is by being cautious about who you share your device with. If you must share your device with someone else, create a separate user profile for them to use, and ensure that they use a strong and unique password.
Overall, limiting access to your work devices is a crucial aspect of remote work security. By implementing best practices like strong passwords, user profiles, and device locking, you can help prevent unauthorized access to your work-related files and data.
However, even with the best security practices in place, accidents can still happen. That’s why it’s important to regularly back up your data. In the next section, we’ll explore the significance of data backups and best practices for backing up your work data.
Regularly back up your data

Data is the backbone of any remote work setup. It’s essential to ensure that you never lose your valuable work data due to any unforeseen circumstances. Regular backups of your data ensure that you always have access to your work even if your device crashes, gets lost or stolen, or if any other disaster occurs. Here are some tips to help you back up your data securely:
- Automate your backups: Schedule automatic backups of your data to ensure you don’t forget to do it manually.
- Use secure backup methods: Use secure cloud-based backup solutions that encrypt your data and keep it safe from hackers and other unauthorized access.
- Choose the right backup location: Select a secure backup location that is geographically dispersed from your primary work location. This way, even if a natural disaster occurs, your data is safe and can be retrieved from another location.
- Back up your data regularly: The frequency of your backups depends on your work volume and the type of data you create. However, it’s good practice to back up your data at least once a week.
Data backups are the key to the success of any remote work setup. By regularly backing up your data, you can ensure the safety of your work and avoid any unpleasant surprises. Make sure to prioritize data backups and follow these best practices to ensure that your data is always safe and accessible.
Cloud-based vs. local backup solutions
Data is everything, and losing it can be catastrophic for a business. This is why it’s crucial to have a reliable backup system in place.
Cloud-based Backup Solutions
Cloud-based backup solutions have become increasingly popular in recent years. They offer a number of benefits, including:
- Accessibility: Cloud-based backups can be accessed from anywhere with an internet connection, making them ideal for remote workers.
- Scalability: Cloud-based backups can easily be scaled up or down depending on the needs of the business.
- Automatic backups: Many cloud-based backup solutions offer automatic backups, ensuring that data is always up to date.
- Security: Cloud-based backup solutions typically offer strong security features, such as encryption, to keep data safe from hackers.
Here are some of the most popular cloud-based backup solutions:
- Google Drive: Google Drive is a popular cloud-based storage solution that offers 15 GB of free storage. It also offers automatic backups, which can be scheduled to run at specific times.
- Dropbox: Dropbox is another popular cloud-based storage solution that offers 2 GB of free storage. It also offers automatic backups, which can be scheduled to run at specific times.
- Box: Box is a cloud-based storage solution that offers 10 GB of free storage. It also offers automatic backups, which can be scheduled to run at specific times.
- Microsoft OneDrive: Microsoft OneDrive is a cloud-based storage solution that offers 5 GB of free storage. It also offers automatic backups, which can be scheduled to run at specific times.
- Amazon Drive: Amazon Drive is a cloud-based storage solution that offers 5 GB of free storage. It also offers automatic backups, which can be scheduled to run at specific times.
- iCloud: iCloud is a cloud-based storage solution that offers 5 GB of free storage. It also offers automatic backups, which can be scheduled to run at specific times.
Local Backup Solutions
While cloud-based backup solutions are becoming more popular, local backup solutions still have their place. Local backups offer a number of advantages, including:
- Control: With a local backup solution, businesses have full control over their data, which can be reassuring for those who are wary of cloud-based solutions.
- Speed: Local backups can be faster than cloud-based backups, particularly if the data being backed up is large.
- No recurring costs: Cloud-based backups often come with recurring costs, while local backups typically have a one-time cost.
When deciding between cloud-based and local backup solutions, it’s important to consider the specific needs of your business. For many businesses, a combination of both cloud-based and local backups may be the best option, as this provides redundancy and ensures that data is always available, no matter what happens.
In the end, the most important thing is to have a backup solution in place. Without one, you’re putting your business at risk of losing everything. So take the time to evaluate your options and choose a backup solution that works for you.
Conclusion
In this fast-evolving world of remote work, it’s crucial to ensure that we’re taking all the necessary precautions to protect our data and devices. Implementing these 10 remote work security best practices can go a long way in providing the necessary safeguards to keep you and your team safe from cyber threats.
Remember to secure your Wi-Fi network, use strong passwords and a password manager, install and update antivirus software, keep software and operating systems updated, implement two-factor authentication, be cautious of phishing attempts, securely store and share sensitive data, limit access to your work devices, regularly back up your data, and educate yourself and your team on cybersecurity.
By following these best practices, you can enjoy the flexibility and convenience of remote work while also having peace of mind knowing that you’re taking the necessary steps to protect yourself and your organization.
So, go ahead, get started, and don’t forget to stay vigilant in the face of ever-evolving cyber threats.
